Account Takeover Fraud: How It Happens and How to Prevent It

Key Takeaways
- ATO attacks often begin with phishing, credential stuffing, or malware that silently steals your login details.
- Victims don’t just lose money but they may lose access to banking, email, crypto wallets, and sometimes their entire digital identity.
- Reused passwords and missing 2FA are the easiest doors hackers walk through and most people still leave them wide open.
- Early red flags like password reset emails or strange charges often go ignored until it’s too late.
- Guardio helps prevent account takeovers before they even begin, offering proactive, cross-device protection that keeps your accounts safe and highlights which accounts or settings need attention, while blocking phishing sites, removing harmful browser extensions, and alerting you to data breaches.
Account takeover fraud (ATO) occurs when cybercriminals gain unauthorized access to your online accounts - whether email, banking, social media, or cloud services - and operate them as if they were you. Once inside, they can drain your funds, steal sensitive personal information, impersonate you, or even commit full-scale identity theft.
These attacks often begin with familiar tactics: phishing emails disguised as legitimate requests, login credentials leaked in a data breach, or malware silently recording your keystrokes. From there, the intruder may lock you out, make unauthorized purchases, alter your account settings, or use your identity to target friends, colleagues, or customers with scams.
The impact can be swift and devastating, but ATO is far from inevitable. By adopting strong, unique passwords, enabling two-factor authentication (2FA), and exercising caution with suspicious links and downloads, you can significantly reduce your risk. In this article, we’ll break down how account takeover fraud works, who is most vulnerable, the warning signs to watch for, and the practical steps you can take to protect your accounts and recover quickly if the worst happens.
{{component-cta-custom}}
What is Account Takeover Fraud (ATO)?
Account Takeover Fraud (ATO) is when a cybercriminal gets access to one of your personal or business accounts, like your email, bank app, or social media, and takes full control. They use stolen credentials, fake login pages, or malware to break in, then lock you out, steal data, transfer funds, or impersonate you.
What makes ATO especially dangerous is that it doesn’t stop at one account. Many people reuse passwords or have connected apps, so once attackers breach one, they often move laterally from email to bank, from Facebook to Instagram, from personal to professional.
According an FBI report, 22% of U.S. adults have fallen victim to account takeover scams, losing an average of $12,000. Learn how to protect yourself from this common attack. 👇 https://t.co/gVIJ6P0DGe
Guardio (@GuardioSecurity) January 2, 2024
ATO has exploded in recent years because login data is everywhere. Billions of usernames and passwords are hacked every year, sold on the dark web, and fed into automated bots that try them on dozens of sites. It’s not some abstract hacker story, it’s a growing, everyday risk. ATO is silent, fast, and very real - and it can happen to anyone.
How Account Takeover Fraud Happens: Common Methods
Cybercriminals don’t need to break down firewalls to steal your account. They use smarter, sneakier tricks. Here are the most common ways attackers take over accounts today:
1. Phishing and Scam Links
You receive a message that appears to come from a trusted source like your bank, a delivery service, or even your workplace. It urges you to click a link or verify your login. But the site is fake, designed to steal your credentials the moment you type them in. According to the FBI’s Internet Crime Report, phishing is the most reported cybercrime every year.
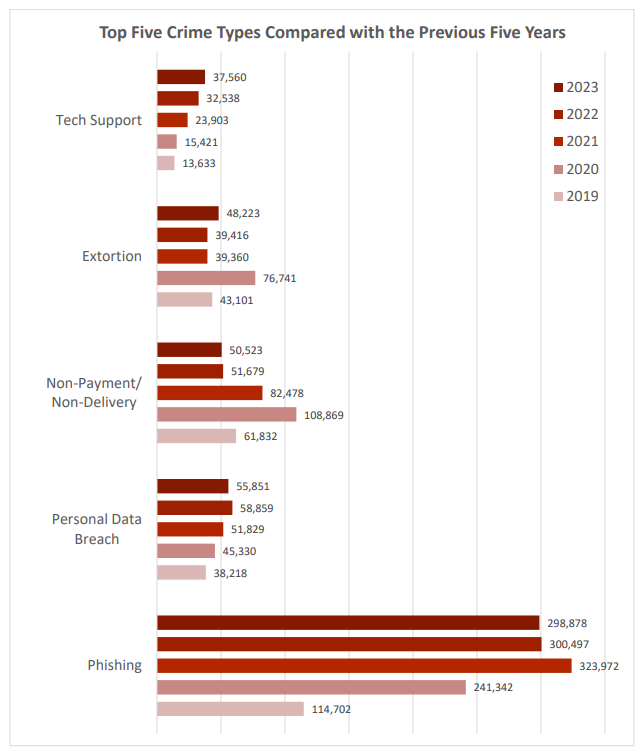
Phishing consistently shows the highest number of incidents across all years, with a notable increase from 2019 to 2023, peaking at 323,972 in 2021.
2. Credential Stuffing Attacks
When companies suffer data breaches, login details often end up for sale on the dark web. Attackers use automated tools to try those credentials across many platforms like banking, email, shopping sites, etc., hoping you’ve reused your password. Unfortunately, many people do.
3. Malware and Keyloggers
Certain types of malware quietly install themselves through unsafe downloads or shady browser extensions. Once active, they can track what you type (including passwords), capture screenshots, or even hijack your browser sessions, all without raising a red flag.
4. SIM Swap and Man-in-the-Middle Attacks
In a SIM swap, attackers trick your mobile provider into assigning your phone number to a new SIM card. This gives them access to text-based two-factor authentication (2FA) codes. Similarly, man-in-the-middle attacks intercept your data on public Wi-Fi, allowing hackers to steal sensitive information during transmission.
5. Weak or Missing Two-Factor Authentication
Relying only on a password, even a strong one, leaves your account vulnerable. Without 2FA, a stolen password is often enough to take full control. Enabling 2FA (preferably via app-based or hardware keys) adds an essential second layer of protection.
Early Warning Signs of Account Takeover Fraud
Account takeover often starts quietly but if you know what to look for, you can act before the damage is done. Here are the most common red flags:
Suspicious Login Alerts
Most platforms (like Google, Microsoft, and Facebook) notify you when there’s a login from a new device, location, or browser. If you see a login alert you don’t recognize, especially from another country or at an odd hour, treat it as a major warning sign.
Password Reset Messages You Didn't Request
Getting a password reset email or text without asking for one? Someone may be trying to take control of your account.
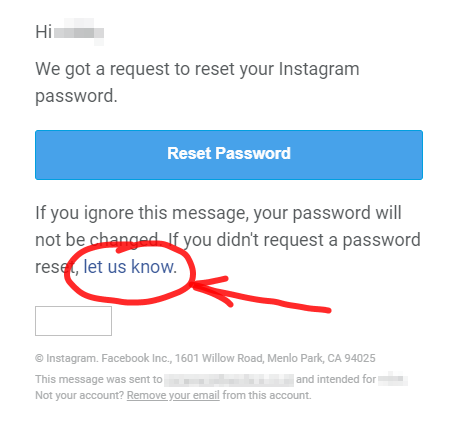
Change your password and enable two-factor authentication immediately. And also report the platform.
Locked Accounts or Access Issues
If you’re suddenly logged out of your account, or your usual password doesn’t work, it could mean an attacker has already changed your login credentials and locked you out.
Unusual Charges or Account Activity
From unexpected purchases to strange emails sent from your account, any behavior that feels off should be investigated. Even small, unexplained charges may be test transactions to check if your card is active before larger fraud attempts.
Consequences of Account Takeover Fraud
An account takeover doesn’t just mess with your login, but it can flip your digital life upside down. Here’s what’s at stake when someone else gains control of your accounts:
1. Financial Losses and Drained Accounts: Hackers often act fast. Once inside your banking or payment app, they may transfer funds, make purchases, or rack up charges on linked cards. Many victims only notice after the damage is done, and recovery can take weeks, even months.
2. Identity Theft and Credit Damage: With access to your email or personal documents, attackers can gather enough information to open credit cards, take loans, or file fraudulent tax returns in your name. This can severely damage your credit score and create long-term financial problems.
3. Loss of Access to Key Services: Losing control of your email can mean losing access to everything else, from cloud backups to work tools. If your social accounts are taken over, scammers may impersonate you, post harmful content, or message your contacts with fake requests.
4. Reputational Harm: When someone uses your identity to scam others, post inappropriate content, or send spam, your reputation takes the hit. This is especially harmful for professionals, influencers, or business owners who rely on digital trust.
Who is Most at Risk of Account Takeover?
While anyone can be a victim of ATO, certain groups face a much higher risk due to their habits, work style, or digital exposure:
| User Group | Why They’re at Risk |
|---|---|
| Remote Workers and Freelancers | Use multiple online tools, often on personal devices with varying security levels. |
| People Reusing Passwords Across Sites | One leaked password can give attackers access to many accounts. Still very common. |
| Seniors and Less Tech-Savvy Users | More likely to fall for phishing emails or use weak passwords. Often unaware of 2FA. |
| Online Shoppers and Social Media Users | Frequently enter credentials or payment info on multiple platforms, sometimes risky or fake ones. |
If you fall into any of these groups, extra caution and stronger security habits are essential because attackers are counting on you not paying attention.
Best Practices to Stay Safe from Account Takeover Fraud
You don’t need to be a cybersecurity expert to protect yourself from account takeover, but just a few smart habits can make all the difference. Here’s what works:
- Use Strong, Unique Passwords: Never reuse the same password across sites. Use long, complex combinations (think passphrases or 12+ characters), and consider a password manager to keep track. This step alone stops most credential stuffing attacks.
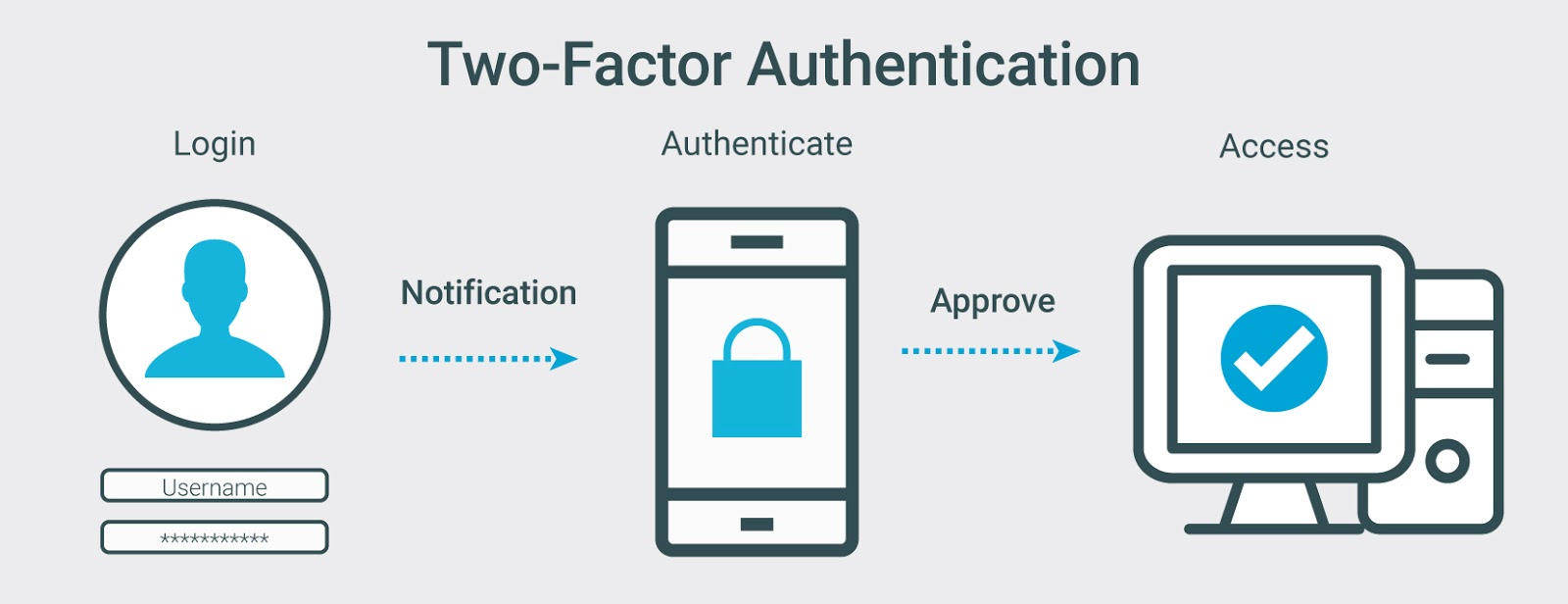
- Turn on Two-Factor Authentication (2FA): 2FA adds an extra layer of protection. Even if someone has your password, they won’t get in without the second step, like a code from your phone or an app. Choose app-based or hardware keys over SMS when possible.
- Be Cautious with Emails and Links: If an email or message feels suspicious, don’t click. Phishing scams often look nearly identical to real company emails. Always double-check the sender’s address and avoid entering passwords from email links.
- Regularly Monitor Your Accounts: Review your account activity often. Look for strange logins, unfamiliar devices, or suspicious charges. The sooner you spot something off, the faster you can act.
- Check for Weak Links in Your Accounts: Use tools like Guardio to scan for reused passwords, missing two-factor authentication, and outdated security settings. It highlights exactly what’s vulnerable so you can fix it before attackers find and exploit it.
Steps to Take If Your Account is Taken Over
If you suspect your account has been compromised, don’t panic, but act immediately. Speed is critical in limiting the damage. Follow these steps right away:
1. Secure the Affected Account Immediately: Try to log in and change your password. If you’re locked out, use the platform’s account recovery tools. Enable two-factor authentication (2FA) immediately after regaining access.
2. Reset Passwords on Linked Accounts: Attackers often use access to one account to break into others, especially if you reuse passwords. Update passwords for any account that shares login details or is linked to the compromised one (like email or payment services).
3. Notify Contacts and Affected Services: Let your contacts know not to trust messages sent from your account. If it’s a work email or social profile, alert your team or followers. For financial accounts, call the bank or provider immediately to freeze activity.
4. Report the Incident to the Platform: Most platforms have dedicated pages for reporting compromised accounts. File a report and follow their steps for account recovery and investigation. It also helps them track and stop future attacks.
5. Scan for Malware or Unauthorized Extensions: Use a trusted anti-malware tool or browser protection service to check your device for keyloggers, spyware, or suspicious extensions. If one account was breached, your device might still be vulnerable.
{{component-tips}}
How Guardio Helps Prevent Account Takeover Fraud
Guardio is a proactive security platform that protects your digital identity across accounts, devices, and online activity. It combines real-time threat detection, phishing protection, and breach monitoring to help you stop attacks before they start, no matter where they come from:
- Blocking Phishing and Malicious Sites in Real-Time: Guardio automatically blocks fake websites that try to steal your login info. Whether it’s a phishing email or a shady pop-up ad, it stops you from landing on dangerous pages in the first place.
- Alerting Users About Data Breaches Linked to Their Accounts: If your email or credentials show up in a known data breach, Guardio lets you know immediately by giving you a head start to change your passwords before attackers try them.

- Detecting and Removing Hidden Threats: From malicious extensions to risky scripts or unknown permissions, Guardio identifies threats that compromise your security posture and removes them before they do harm.
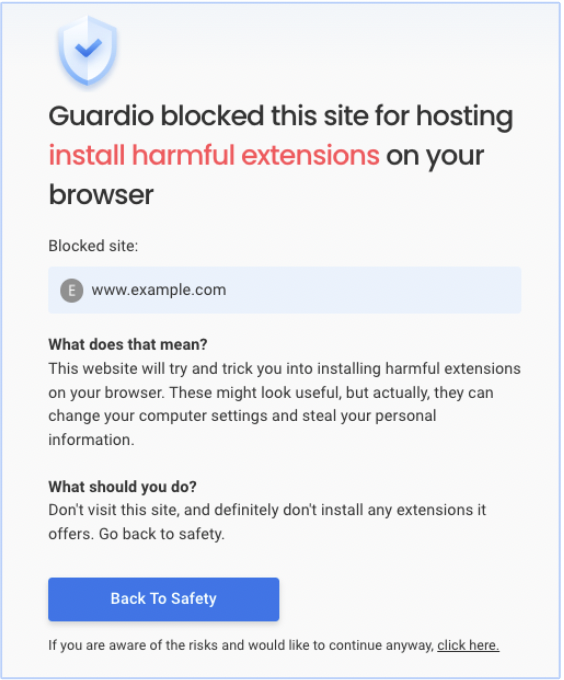
- Proactive, Always-On Protection for Your Accounts: Guardio continuously monitors for threats in real time, alerting you to security risks, data breaches, and weak account settings before attackers can exploit them. Instead of waiting for manual checks, it keeps you protected as you manage and use your accounts.
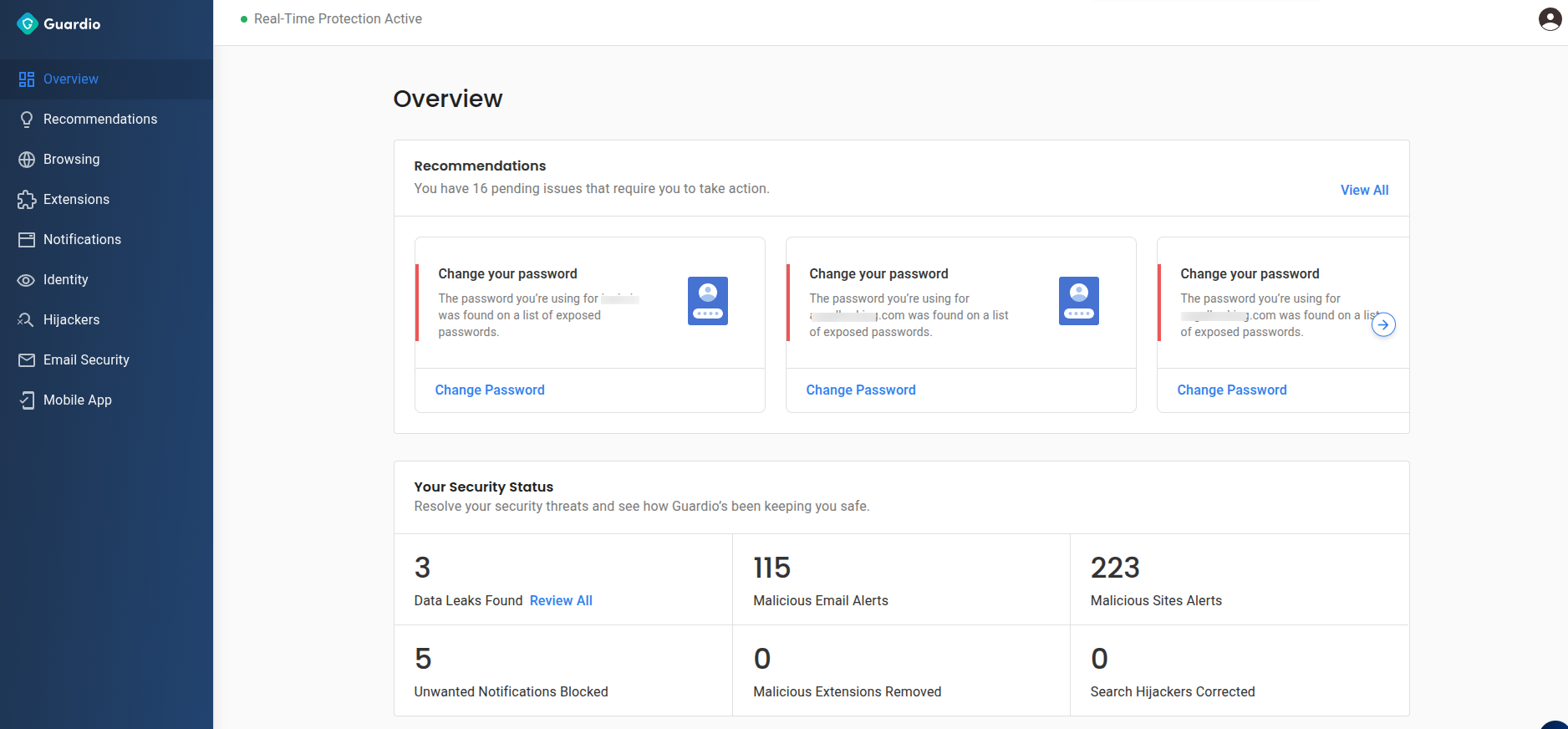
- Lightweight, Privacy-Focused Security: Guardio runs quietly in the background, protecting your accounts and personal information without compromising your device performance or privacy.
Conclusion
Account takeovers happen every day, often silently, affecting millions of people around the world. Whether it’s your email, bank, or social media, a single compromised account can lead to financial loss, identity theft, and serious disruptions in your life.
By using strong, unique passwords, enabling two-factor authentication, staying alert to phishing attempts, and monitoring your accounts regularly, you can block most takeover attempts before they even begin. And for extra peace of mind, tools like Guardio provide real-time, device-level protection by stopping malicious websites, flagging data breaches, and removing dangerous extensions before they compromise your security.
{{component-cta-custom}}








