Amazon Refund Scams: What Just Changed and How to Stay Safe

Key Takeaways
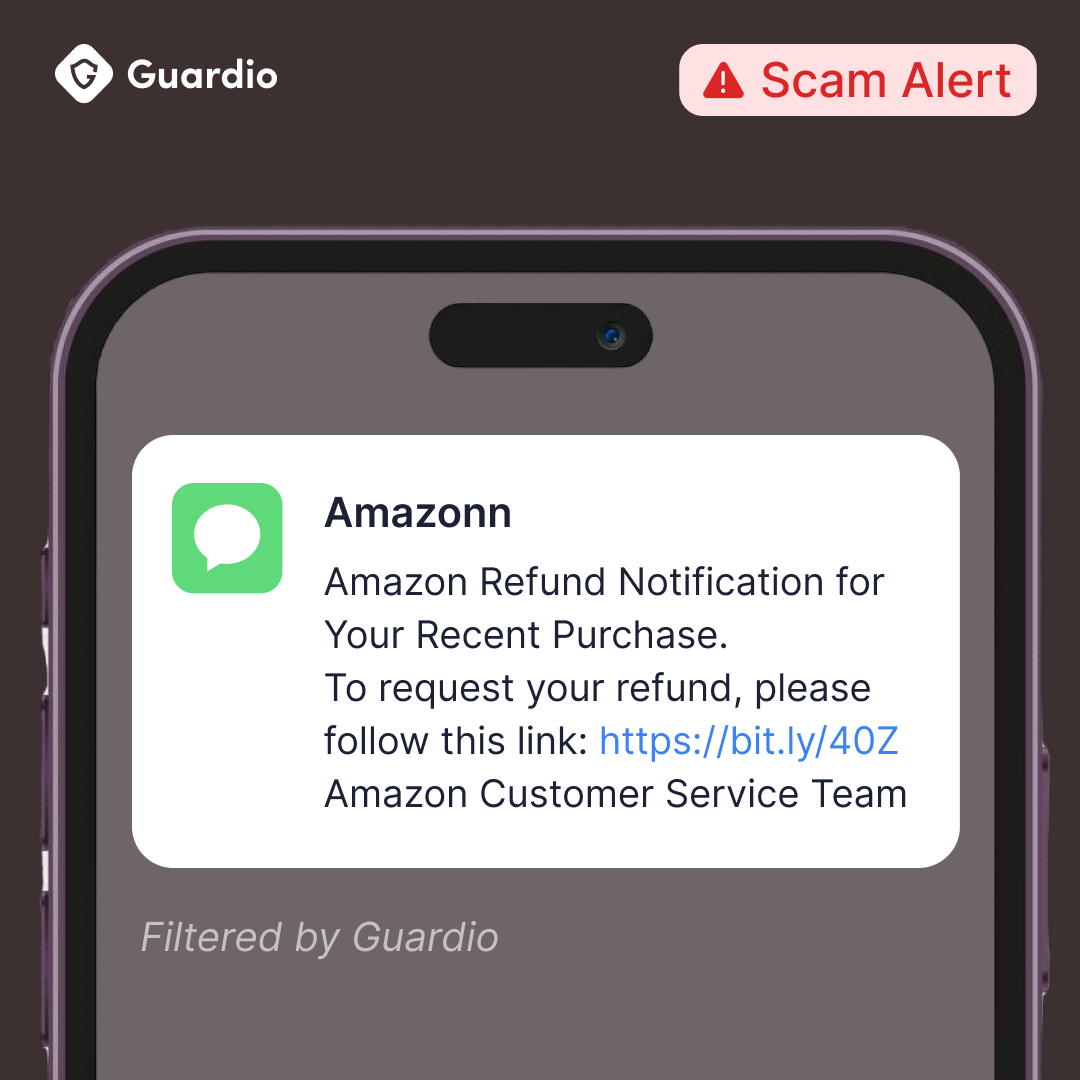
Have you received a text claiming Amazon owes you a refund for a recalled product? If yes, think twice before clicking on it.
Amazon refund scam texts have exploded by 5,000% since Prime Day in July 2025, creating an unprecedented wave of phishing attacks targeting millions of shoppers. Guardio's cybersecurity researchers were the first to detect this massive surge, with their findings prominently featured in Forbes as the threat reached crisis levels.

Furthermore, the timing of this surge makes it especially dangerous. Many consumers are genuinely expecting legitimate refunds from recent purchases, making them more likely to fall for these convincing fakes. The Federal Trade Commission quickly issued official warnings following Guardio's discovery, and major news outlets like the Houston Chronicle, continue sounding alarms as the scam spreads.
These were not conventional scams. Attackers have evolved their tactics, using fake order numbers, convincing recall notices, and urgent refund offers that exploit our trust in Amazon. Worse yet, traditional security solutions were unable to stop these sophisticated attacks because they rely on recognizing known threats. But these scams were designed to be nearly indistinguishable from legitimate Amazon communications. This meant what was needed wasn't just another security tool, but real-time threat detection like Guardio's that could identify brand-new attack patterns the moment they emerged
Far more sophisticated than most people realize, what's really happening behind these messages means your current defenses probably won't be enough to stop what's coming next, unless you know exactly how to protect yourself.
What Are Amazon Refund Scams?
Amazon refund scams are sophisticated phishing attacks where cybercriminals impersonate Amazon through text messages and emails, claiming there's a problem with your recent purchase and offering an immediate "refund" through a malicious link.
But here's what makes these scams particularly insidious: they don't just randomly target people hoping someone will bite. These attacks have been carefully designed to exploit the one thing nearly every American has in common: their trust in Amazon.
The messages themselves have evolved far beyond the obvious spam of years past. Instead of broken English and obvious red flags, today's Amazon refund scams arrive looking remarkably legitimate. You might receive a text claiming: "Amazon Quality Control: Your recent order #AMZ-7429-8851 failed our routine inspection. Full refund available, no return required. Claim here: [malicious link]".
Other common variations include messages about "return processing issues," notifications that "the seller's store has been permanently closed for policy violations," or urgent alerts about product recalls affecting your recent purchases. Each message follows the same dangerous playbook: create urgency, offer something valuable (money back), and provide a convenient solution (click this link).
These messages are more than just visually convincing; they exploit a moment when consumers are most vulnerable. Many people have recently shopped on Amazon or are expecting refunds, making the scam feel alarmingly relevant and urgent. It's a psychological trap that lowers your defenses by targeting your anticipation and trust.
And once your guard is down, that's when the real damage begins. The link in every message leads to the same destination: a fake Amazon website designed to steal your login credentials, payment information, and personal details. Once scammers have this information, your real Amazon account becomes their playground.
Summing up, the most common scam messages claim:
- Refund available for recent purchases
- Return processing issues requiring immediate action
- Store closures due to policy violations
- Product recalls with urgent refund offers
- Fake order numbers to appear legitimate
This is just the beginning of how deep this problem goes.
What Just Changed?
This isn't just another wave of scams; it's a fundamental shift in how cybercriminals operate. The Post-Prime Day surge revealed that scammers have abandoned their old spray-and-pray approach for something far more sophisticated: strategic opportunism.
Instead of casting wide nets with obvious phishing attempts, they now time their attacks to coincide with moments when consumers are most receptive. Prime Day created the perfect storm: millions of people making purchases, expecting deliveries, and anticipating potential issues or refunds. Scammers didn't just notice this opportunity; they weaponized it.
What makes this evolution particularly dangerous is the speed of adaptation. Within days of Prime Day ending, these criminals had already refined their messaging, incorporated fake order numbers, and created convincing scenarios that traditional security systems weren't prepared to handle, as detailed by Dataconomy and SlashGear.
This represents a turning point where reactive cybersecurity measuresdetecting threats after they've been identifiedare no longer sufficient. Scammers are now moving faster than the security industry's ability to catalog and block new threat patterns.
The question isn't whether these attacks will continue evolving; it's whether your current defenses can keep pace with criminals who are becoming increasingly strategic about when, how, and whom they target.
Why They're So Convincing
Let’s recap on why these messages have been so effective:
- Amazon's widespread trust gives these scams instant credibility: With 75% of Americans holding Prime subscriptions, a message from "Amazon" doesn't immediately raise red flags.
- The timing was calculated: These attacks hit when people genuinely expect Amazon communications, right after major sales events or recent purchases. Picture receiving a "refund available" text just days after Prime Day shopping; your guard naturally drops.
- Scammers weaponize emotions: urgency ("act now"), fear of loss ("limited time"), and FOMO ("don't miss your refund") that push people to click before thinking clearly.
Consumer discussions on platforms like Reddit reveal how even tech-savvy users initially found these messages convincing, sharing experiences of near-misses with increasingly sophisticated scam attempts.
Here's why conventional security fails against these attacks: Most security tools rely on blacklists of known malicious URLs or recognizable spam patterns. But these scams use fresh domains, short-code links that redirect through legitimate services, and messages that haven't been flagged yet. A traditional antivirus might block "known-bad-site.com" but miss "amzn-refund[.]tk" redirecting through a clean URL shortener.
Moreover, these solutions aren't built for psychological manipulation: they can't detect that a perfectly legitimate-looking message is designed to exploit human psychology. That's why even tech-savvy users with premium security software fall victim.
This gap between technical protection and human vulnerability is exactly why next-generation solutions focusing on real-time behavioral detection are becoming essential.
Now, let's explore exactly how to protect yourself.
Guardio's Role
When Guardio detected the 50x spike in Amazon refund scams after Prime Day 2025, it revealed something crucial: these attacks were specifically designed to exploit gaps in how people use technology today.
Consider this common scenario: you're shopping on Amazon during lunch at work on your laptop, then later that evening you get a text on your phone about a "refund issue" with that exact order.
Traditional security might protect your work computer, but it misses the mobile text scam entirely.
Guardio's holistic approach monitors your digital life across all devices and accounts, connecting these dots to recognize when scammers are targeting you personally across multiple touchpoints.
Here's what makes Guardio different: while conventional security waits to recognize known threats, Guardio's next-generation AI identifies suspicious behavior patterns instantly. When scammers created those convincing fake Amazon messages with fresh URLs and realistic order numbers, traditional tools had no database entry to reference. But Guardio's behavioral analysis spotted the psychological manipulation tacticsthe urgency, the trust exploitation, the timingand blocked these messages before they could deceive users.
The human-centric design means Guardio understands that the average person isn't a cybersecurity expert. Instead of overwhelming technical alerts, it provides clear guidance: "This message is trying to steal your Amazon login; here's what to do." This approach acknowledges that today's scams target human psychology, not just technical vulnerabilities.
When major outlets like Forbes, SlashGear, and Dataconomy featured Guardio's findings, it validated something important: real-time threat intelligence that adapts as quickly as scammers evolve is no longer optionalit's essential. Guardio empowers everyday users by staying one step ahead of threats designed to exploit our trust and habits.
How to Protect Yourself
Taking control starts with these essential steps:
- Never click links in unsolicited messages claiming to be from Amazon, regardless of how legitimate they appear
- Verify refund claims directly by logging into the official Amazon app or website; never through message links
- Ignore order numbers in suspicious texts; scammers insert fake ones specifically to create false legitimacy
- Report and delete immediately: Forward suspicious texts to 7726 (SPAM) and delete the message
- Enable Two-Factor Authentication (2FA) or passkeys on your Amazon account for critical additional security
- Protect yoursef with solutions like Guardio that provide real-time phishing detection across all your devices, adapting instantly to new threats without requiring constant user vigilance
Building multiple defense layers is key. While these manual steps provide essential protection, the rapidly evolving nature of these scams means automated, intelligent protection is becoming necessary to stay ahead of next-generation threats.
Remember: these scammers are becoming more strategic and faster-moving every day. Your protection needs to evolve at the same pace to remain effective.
Conclusion
The recent surge in Amazon refund scams represents more than just another cybersecurity threat: it's a wake-up call about how quickly scammers adapt to exploit our trust and habits. These sophisticated attacks combine brand familiarity, perfect timing, and psychological manipulation to bypass traditional defenses and target the one vulnerability most security tools can't protect: human nature.
But knowledge is power. Understanding how these scams work, recognizing their tactics, and implementing the right protective measures puts you back in control. Whether it's manually verifying suspicious messages through official channels or deploying next-generation protection like Guardio's real-time threat detection, you now have the tools to stay ahead of evolving threats.
The question we started with: Have you received a suspicious Amazon refund text? no longer needs to create anxiety. Armed with awareness and proper protection, you can confidently navigate your digital life without falling victim to even the most convincing scams.
Stay vigilant, stay protected, and remember: scammers may be getting smarter, but so are you. For more insights on protecting your Amazon account, check out our guide on what to do if your Amazon account gets hacked.








