Top Signs of Dropbox Scams and How to Respond Safely

Key Takeaways
- Dropbox scams are designed to look legitimate, often using fake shared files or login pages to steal credentials.
- Common warning signs include urgent file requests, mismatched URLs, and unusual sender email addresses.
- Once a malicious Dropbox link is clicked, quick action like changing passwords, logging out of sessions, and scanning for malware can limit damage.
- Limiting sharing permissions, removing unused integrations, and enabling two-factor authentication significantly reduces scam risk.
- A security solution like Guardio proactively spots weak points in your online security, flagging risky links, stopping malicious downloads, alerting you to exposed credentials, and guiding you to secure vulnerable accounts before attackers exploit them.
As one of the most widely used cloud storage platforms, Dropbox has become an essential tool for businesses and individuals alike. Its convenience, however, has also made it a prime target for cybercriminals. Increasingly, attackers are exploiting the trust people place in Dropbox to deliver phishing links, steal credentials, and distribute malware.
Dropbox scams are no longer limited to obvious spam or poorly written emails. Many now closely mimic legitimate file-sharing requests, impersonate trusted colleagues, or abuse compromised accounts, making them difficult to detect at a glance.
This article outlines the most common forms of Dropbox-related scams, how to recognize them, and the steps you should take to protect yourself and your organization. It also includes real-world examples and response protocols if exposure occurs. By understanding the tactics behind these threats, you’ll be better equipped to prevent data loss, account compromise, and potential breaches.
{{component-cta-custom}}
What Are Dropbox Scams?
Dropbox scams are fraudulent schemes where cybercriminals misuse the Dropbox platform or create convincing imitations of it to trick you into taking risky actions. These attacks may aim to steal login credentials, install malware, or gain unauthorized access to sensitive files and data.
Scammers often exploit the trust people place in Dropbox. They might send fake file-sharing invitations, build lookalike login pages, or use already-compromised accounts to spread malicious links. Because these messages appear to come from a familiar platform, or even someone you know, victims often click without double-checking.
Many Dropbox scams are part of larger phishing or social engineering campaigns designed to infiltrate personal or business accounts. Falling for one can lead to data theft, financial loss, and even wider network breaches.
In short, a Dropbox scam is any tactic that uses the Dropbox brand or platform, through impersonation or misuse, to compromise your accounts, devices, or information.
Types of Dropbox Scams
Cybercriminals use several tactics to exploit the Dropbox platform or its brand. Understanding these methods can help you identify threats before they cause damage:
Phishing Links Shared Through Dropbox Files
In this type of scam, attackers upload a document to Dropbox that contains links to malicious websites. The document may appear to be a legitimate report, invoice, or form.
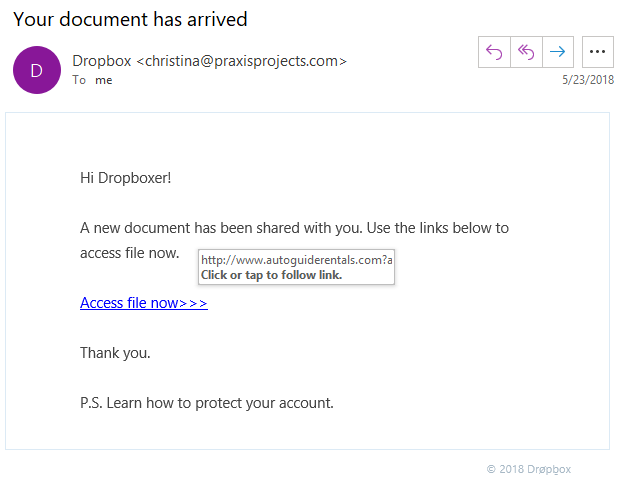
Once opened, it encourages the reader to click a link that leads to a phishing page designed to steal personal or account information.
Fake Login Pages That Mimic Dropbox
Scammers create web pages that look almost identical to Dropbox’s official login screen. Victims are tricked into entering their credentials, which the attacker then captures and uses to access the real Dropbox account.

These fake pages are often delivered via email or instant message links.
Fake Shared Files or Folders
Attackers send messages claiming that a file or folder has been shared with the recipient. The link, however, does not lead to a real Dropbox resource. Instead, it may download malware or redirect to a phishing site. Because Dropbox sharing is common in professional environments, these scams can be particularly effective.
Impersonation of Colleagues or Business Partners
In some cases, scammers compromise an email account or register an address similar to that of a trusted contact. They then send Dropbox links that appear to come from a known source. Recipients are more likely to click and download the file without question, increasing the risk of infection or data theft.
Malicious Third-Party App Integrations
Dropbox supports integration with various third-party applications. Scammers exploit this feature by convincing users to authorize a malicious app that has access to files, folders, or account settings. Once access is granted, the attacker can copy, alter, or share data without the user’s knowledge.
How to Recognize a Dropbox Scam
Dropbox scams often look convincing, but certain warning signs can help you identify them before you click:
| Sign of a Possible Scam | What It Means | Why It’s Risky |
|---|---|---|
| Unexpected Dropbox file sharing requests | Receiving a file or folder you were not expecting, with no context or prior conversation | May lead you to open malicious files or links |
| Urgent messages pushing immediate action | Messages that claim a document needs instant review or your account will be suspended | Designed to pressure you into skipping security checks |
| Link previews that do not match real Dropbox URLs | Hovering over a link reveals a misspelled or unfamiliar domain instead of dropbox.com or dropboxusercontent.com | Links may lead to phishing sites or malware downloads |
| Emails imitating Dropbox or internal HR | Professional-looking emails that contain small errors in grammar, formatting, or branding | Tricks recipients into thinking the message is legitimate |
| Suspicious or misspelled sender email addresses | Sender address closely resembles a trusted one but contains slight changes, such as numbers replacing letters | Can make you trust a scammer’s message and click harmful links |
Recognizing these warning signs early can help you avoid clicking harmful links, sharing sensitive information, or compromising your Dropbox account.
Real-World Dropbox Scam Examples
While scams can take many forms, real incidents reveal just how convincing and targeted these attacks can be. Below are some notable examples of how cybercriminals have exploited Dropbox to trick individuals and organizations.
Fake Dropbox Files Shared During Tax Season
During tax season, scammers often send Dropbox links that claim to contain important tax forms or financial statements. These links may lead to phishing pages designed to capture personal information or download malicious files. The timing increases the likelihood that recipients will click without verifying the source.
Dropbox Links with Malicious Business Documents
Attackers frequently impersonate vendors, clients, or business partners to share supposed contracts, invoices, or project files. In reality, the documents may install malware or ransomware upon opening, putting entire networks at risk.
HR-Themed Dropbox Scams (e.g., Job Offers, Policies)
Some scams are designed to look like they come from a company’s HR department. They may promise a job offer, contain updated policies, or request verification of employee information.
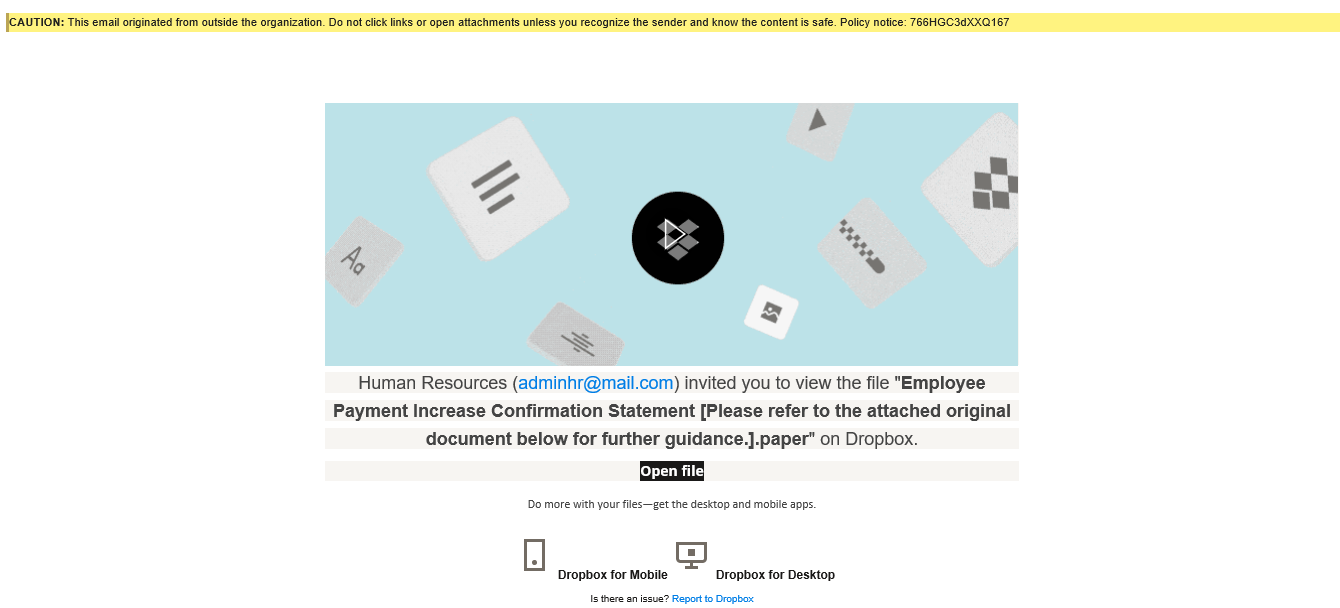
The links often lead to credential theft or malware downloads.
Hacked Dropbox Accounts Sending Scam Files
In certain cases, scammers gain access to a legitimate Dropbox account. They then send malicious links or files to all contacts associated with that account. Because the message comes from a trusted sender, recipients are more likely to engage, making this tactic especially dangerous.
How to Protect Yourself and Your Organization from Dropbox Scams: Best Practices
Protecting against Dropbox scams requires both individual vigilance and organization-wide safeguards. By combining good personal security habits with structured company policies, you can significantly lower the chances of a successful attack. The following best practices cover both user-level actions and advanced organizational measures.
User-Level Tips
- Create strong, unique passwords for every account: Avoid reusing passwords across services to reduce the risk of multiple account breaches.
- Enable two-factor authentication (2FA) on Dropbox: Adds an extra verification step, making it harder for attackers to access your account even if they have your password.
- Avoid clicking unknown or unverified Dropbox links: Treat unsolicited file-sharing invitations with caution, especially if there is no prior context.
- Always confirm the sender before opening shared files: Contact the person through a known channel to verify the file is legitimate.
- Use layered security tools: Guardio scans for reused passwords, missing two-factor authentication, and risky links, and then gives you clear steps to fix vulnerabilities before attackers find them.
Advanced Organizational Practices
- Train employees to identify Dropbox scam attempts: Conduct regular security awareness sessions and phishing simulations.
- Disable email link previews to prevent auto-loads: Reduces the chance of accidentally visiting malicious sites.
- Review Dropbox sharing permissions regularly: Ensure only authorized users have access to sensitive folders.
- Set expiry dates and passwords on shared links: Limits exposure of files after the intended access period.
- Use domain authentication protocols (SPF, DKIM, DMARC): Helps verify that emails claiming to be from your domain are legitimate.
What to Do If You Clicked a Malicious Dropbox Link
Clicking on a malicious Dropbox link does not have to mean total compromise, but acting fast is critical. The following steps will help you limit potential damage, secure your account, and prevent attackers from gaining further access.
Step 1: Immediately Change Your Dropbox and Email Passwords
Update your passwords right away to prevent attackers from using stolen credentials. Use strong, unique passwords that have not been used for any other accounts.
Step 2: Log Out of All Sessions Across Dropbox Devices
Go to your Dropbox account settings and sign out from all active sessions. This forces any unauthorized users to re-enter credentials, which they will no longer have.
Step 3: Run a Full Malware and Virus Scan
Use reputable antivirus or endpoint protection software to detect and remove any malicious programs that may have been installed.
Step 4: Inform Your IT or Security Team Right Away
If you are part of an organization, notify your IT or security team immediately. They can take steps to secure accounts, investigate the incident, and prevent further spread.
Step 5: Stay Alert for Follow-Up Phishing Attempts
Attackers may target you again, using the information they obtained. Be extra cautious with emails, text messages, or calls requesting sensitive information.
How to Report Dropbox Scams
Actively reporting scams helps protect not only yourself but also your organization and the broader online community. Below is a quick reference on where and how to report suspicious Dropbox activity:
| Action | Purpose | How to Do It |
|---|---|---|
| Forward suspicious messages to abuse@dropbox.com | Alerts Dropbox so they can investigate and take down malicious content | Forward the original email or message without altering the headers |
| Flag and report scam websites | Helps security teams and hosting providers remove malicious sites | Use your browser’s “Report” feature or a threat-reporting site like browser security tools |
| Submit a report to your IT or email administrator | Allows your organization to block threats and check for related incidents | Provide full details, including the suspicious link, sender address, and any screenshots |
| Notify teammates or friends who may also be targeted | Prevents the spread of the scam to people in your network | Send a short warning with the suspicious link or email address to watch out for |
{{component-tips}}
How Guardio Detects and Blocks Dropbox Scams
Guardio stops Dropbox-related scams before they can cause damage by focusing on the three most common attack paths: malicious file downloads, suspicious email sources, and fake login pages. Here’s how it works:
- Blocks harmful file downloads: Stops any file coming from an unverified or flagged Dropbox link before it reaches your device.
- Intercepts fake Dropbox login pages: Instantly blocks credential-stealing sites that mimic Dropbox sign-in screens.
- Flags suspicious emails with Dropbox links: Warns you when an email contains Dropbox links from unknown senders or untrusted sources.
By cutting off these attack paths early, Guardio ensures malicious files never reach your system, phishing pages never capture your credentials, and suspicious messages are identified before you act.
Conclusion
Dropbox scams can lead to serious data breaches, financial losses, and reputational damage. The most valuable defense you have is a combination of awareness, quick action, and layered security. By knowing the different types of scams, recognizing their red flags, and following best practices, you put yourself several steps ahead of attackers.
Security is an ongoing process. Pair user training and least-privilege sharing with continuous protections, such as Guardio’s phishing and download blocking, malicious extension detection, and breach alerts, to convert many Dropbox-themed threats into non-events.
{{component-cta-custom}}








